This article applies only to the firewall in the Cloud Control Panel on our Cloud VM plans.
** NOTE: Don't forget to click Add Rule and Apply Firewall Rules to save your new rule, or if you are editing an existing rule otherwise the changes you saved won't be applied to the firewall itself. **
Please see here for some information on what ports you might want open:
https://help.blacknight.com/entries/22917321-what-ports-should-i-open-to-my-cloud-vm
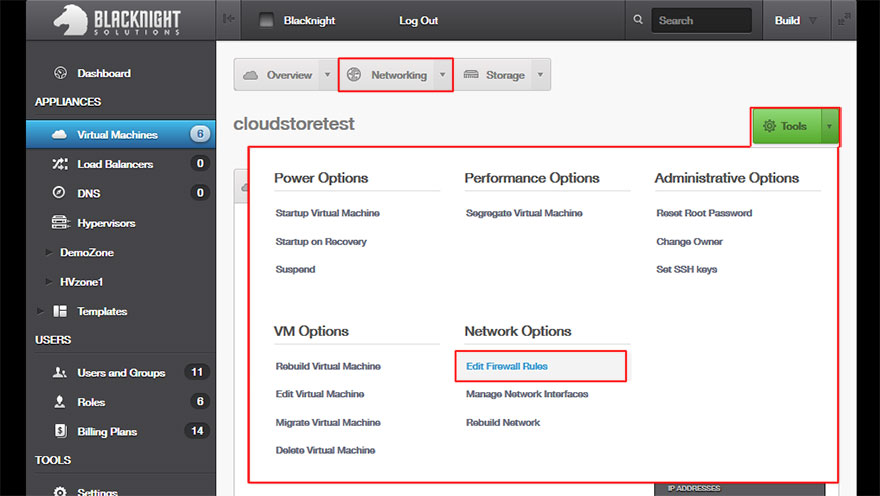
Accessing the Firewall
You can access the firewall in the Cloud Control Panel under:
Virtual Machines > vm name > Networking > Firewall
OR:
Virtual Machines > vm name > Tools > Edit Firewall Rules
Default Firewall rules
Only a small number of ports are open through the firewall by default (for access from anywhere). Those depend on the template you chose when you first bought the VM, if you have since rebuilt the VM with a different template then you might need to add ports to this for access:
Linux template: 22(ssh), 80 (http), 443 (https)
Windows template: 80 (http), 443 (https), 3389 (RDP)
Changing the default policy
If your default policy is set to ACCEPT then by default all access is allowed unless specified by a DROP rule in your rules. This is not recommended unless you have a local firewall such as iptables or Windows Firewall.
We recommend you set the policy to be DROP and set up rules to allow the access you want in.
Opening a port for access from anywhere
Adding a firewall rule
In the firewall page fill in the details you need in the fields provided and press Save, then Apply Firewall Changes. The various fields are:
Interface: has to be eth0, your VM only has one network interface
Command: can be Drop or Accept. Accept opens access to the port, Drop blocks it.
Source Address: Leave blank for access from anywhere, or put in the IP address or netblock range in CIDR format that you want to open\block the port from
Destination Port: The port number you want to open\block
Protocol: TCP would be for most, if not all, of your rules typically as that would be what most applications use, but some use UDP, e.g. DNS over port 53.
Changing the order of rules
The order of your firewall rules does matter. The firewall will process the rules from the top down so if there is a rule allowing access before a drop rule access will still be granted, and vice versa. You should have rules you want to be checked and applied first at the top of the list.
Press the up and down arrows beside the rule in question to change its position. These only work when you have more than one rule.
Disabling the firewall
If you don't want to use the firewall here for any reason you can disable it by changing the Command under Default Firewall Rules from Drop to Accept. Then press Save and Apply Firewall Changes.
Please note that you should have a firewall installed on the VM itself to use in place of this if disabling the firewall here or else you are leaving the VM very vulnerable to compromise. This may help you with that:
Linux: https://wiki.blacknight.com/index.php/IPTables
Windows: https://help.blacknight.com/entries/22916352-how-to-enable-windows-firewall
Some things to note:
# You can only have one TCP and one UDP rule set up with the same "Source" IP address\range.
# There is a maximum of 15 ports allowed in each rule
# If you need to open more than 15 ports from anywhere then any different number of spaces in the Source Address field will count as separate rules, but all allow access from anywhere.
NB: There is currently a glitch with the firewall control on Cloud that can cause the following error when you attempt to apply a new rule:
Rule has not been added. Source Address The combination of three: IP address, port and protocol must be unique., Destination Port The combination of three: IP address, port and protocol must be unique., and Protocol The combination of three: IP address, port and protocol must be unique.
If you encounter this the solution is to remove all firewall rules and re-create them, it should work for you then. This issue is set to be addressed in a future patch, in the meantime, apologies for the inconvenience.
Comments
0 comments
Article is closed for comments.